In today’s digital world, IP addresses and ports are the silent backbones of every online connection. One such example, 172.16.252.214;4300, might look like a random string of numbers, but it actually reveals important details about how networks communicate securely and efficiently. To fully understand its role, it’s crucial to break down what each part represents, how it functions, and why it matters in networking and cybersecurity.
What Is 172.16.252.214;4300?
The sequence 172.16.252.214;4300 is made up of two main components: the IP address and the port number. The IP address 172.16.252.214 identifies a specific device on a private network, while 4300 represents the port used for communication. In simpler terms, the IP address acts like a street address, and the port number works like an apartment number inside that building. Both together define a precise path for data to travel from one device to another.
Breaking Down the IP Address
The IP 172.16.252.214 belongs to the 172.16.0.0 to 172.31.255.255 range, which is reserved for private networks under the IPv4 addressing scheme. This means it’s not publicly accessible on the internet but used internally within organizations, companies, or home networks. Devices on private networks rely on these addresses to communicate without exposing sensitive data to external threats. Such IPs are commonly used in local area networks (LANs), corporate intranets, and VPNs. They help maintain structure and security by keeping internal systems isolated from the public web.
The Role of Port 4300
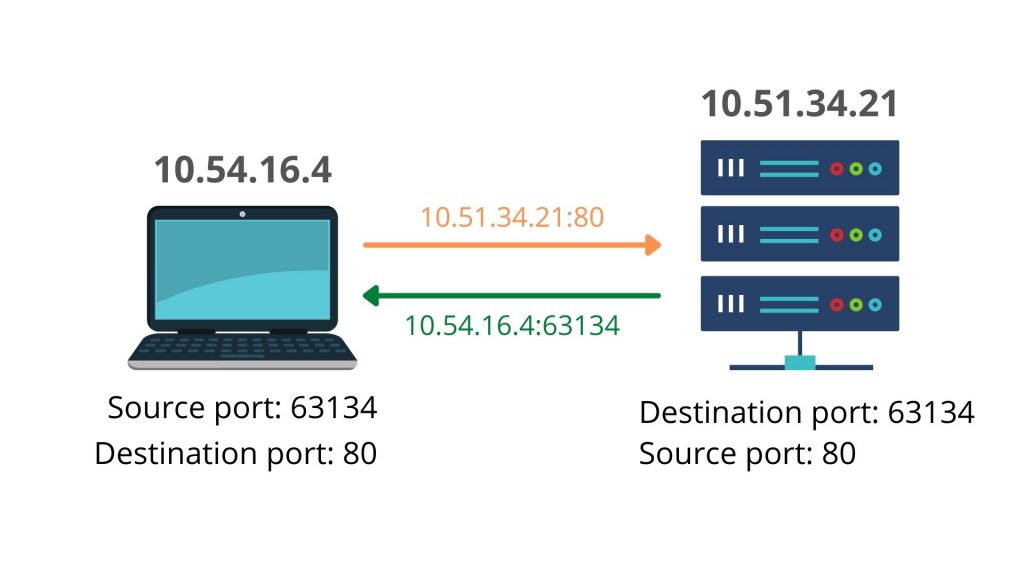
Every IP address can host multiple services, and that’s where port numbers come in. Port 4300 acts as a digital gate that directs data to a specific service or application. When combined with the IP, it forms a unique socket: 172.16.252.214:4300 (noting that the semicolon in the original format is a separator). Port 4300 is often used for custom applications, internal APIs, or system management tools. Network administrators can assign it to specialized services that don’t fit standard ports like 80 (HTTP) or 443 (HTTPS).
How IP and Port Work Together
When a computer sends data across a network, it needs to know exactly where to send it. The IP defines the destination device, and the port tells it which application or process should receive that data. Together, 172.16.252.214;4300 ensures precise routing. For example, one device may host a web service on port 80 and a monitoring system on port 4300. Without ports, data packets could easily get lost or delivered to the wrong process, causing confusion or errors.
Practical Uses in Network Environments
Inside organizations, private IPs like 172.16.252.214 paired with a specific port help run internal software, manage remote servers, or monitor systems. Developers might use such configurations for testing internal APIs or connecting different parts of an enterprise application. IT teams often prefer non-standard ports like 4300 to enhance security, making it slightly harder for unauthorized users to guess where certain services are running. In virtual private networks (VPNs), such combinations are crucial for secure tunneling and controlled access.
Security Considerations
While private IPs are hidden from the public internet, they still require strong internal security. Misconfigured ports can create vulnerabilities. For instance, if port 4300 is unintentionally exposed through port forwarding, it might become an entry point for attackers. That’s why network administrators regularly scan for open ports, apply firewalls, and enforce access control lists (ACLs) to prevent misuse. Using encryption and authentication further strengthens communication between devices using this configuration.
Troubleshooting Connections
If a connection to 172.16.252.214;4300 fails, several factors could be responsible—network misconfiguration, firewall blocks, or service downtime. Diagnosing such issues involves checking whether the device is reachable through ping tests, verifying port availability with tools like Telnet or Nmap, and ensuring the correct protocol is in use. Proper documentation of IP-port mappings is essential in large networks to avoid confusion and downtime.
Conclusion
The combination 172.16.252.214;4300 may look technical, but it embodies how digital systems communicate with precision. The IP represents the device, while the port ensures the message reaches the right program. Together, they form the foundation of secure, structured networking. Whether in corporate infrastructure or home setups, understanding such configurations helps improve performance, reliability, and cybersecurity.